Discover the Differences Between Private, Public, and Hybrid Cloud Services
Learn the Differences Between Private, Public, and Hybrid Cloud Services
Selecting the right cloud service for your business can feel overwhelming when you discover the number of options available is nearly endless.
What’s the difference between a private cloud service versus a public cloud service? What is a hybrid cloud service?
Here are some quick lessons and tips to help you select the right option for your business needs.

CLOUD SERVICE 101
As a business continues to grow and flourish, there needs to exist a data storage strategy that can be efficient, easily accessible, and cost-effective. And let’s not forget about high security! However, choosing the right cloud infrastructure to meet your needs and budget is no easy task.
Technology quickly advances from one day to another, as cybersecurity threats adapt to strengthening firewalls and solutions. So, how are you supposed to figure which options are best for your business needs?
First, let’s cover the basics to help you uncover the right cloud solution:
Private Cloud Service
A private cloud service allows customers the ability to tailor cloud services to meet individual and unique needs. Typically, data is hosted on a dedicated server and provided the bare essentials. This means the customer is responsible for the management, maintenance, and security infrastructure to protect and secure business operations.
Private cloud services are typically selected by companies that are large enough to provide their own team for the responsibility of its service and maintenance, 24/7.
Dedicated hardware and software is fully supported and maintained by your company’s in-house team. No outsiders! There is a lower exposure to security threats since a shared network in non-existent.As the sole owner, all repairs, maintenance, hardware and software upgrades are your responsibility.
Public Cloud Service
A public cloud service relieves customers of the responsibility for the management and maintenance of a dedicated data server. The provider supports, updates, and handles all of the customer’s needs which can be paid for on a monthly or annual service period. In addition to it being budget-friendly, a public cloud is a workplace essential that allows every employee to use the same application from any office or branch with their choice device as long as they have internet access.
Public cloud services are typically selected by companies that do not wish to spend their time and resources maintaining a cloud infrastructure but are looking to benefit from its uses.
Low-cost options are readily available as cloud service providers are responsible for the management and maintenance of data servers. Basic security compliance requirements met. Not ideal for users needing high-security compliance, such as government and medical use. A shared network means the cost of energy and resources can stay low, but can also reduce performance levels.Hybrid Cloud Service
A hybrid cloud service combines the perks of both private cloud solutions and public cloud solutions to fit a variety of business needs. Instead of battling between having all of your IT services on or off an entire data center infrastructure, you can now choose to do both.
Hybrid cloud services are typically selected by companies that wish to have flexibility in service without sacrificing security.
Connect private clouds to public clouds without the risk of leaking confidential information or lessened security. Services can be scaled up or down to meet business demands and ensure you only pay for the space used. By using a combination of private and public cloud services, employees can easily and quickly access files, data, and applications.Check out VPLS Hybrid Cloud Services to learn more or reach out to a VPLS Specialist to discover the many ways in which cloud solutions can help your business run at the top of its game.




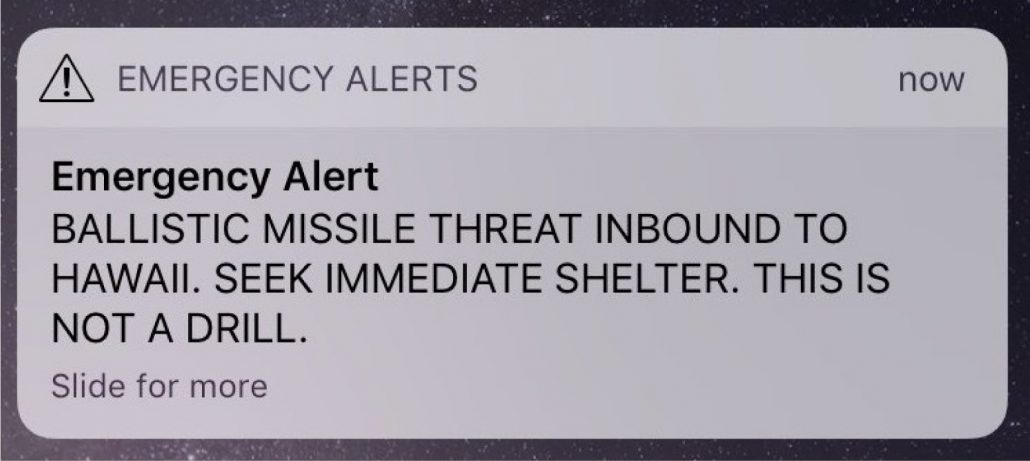 Take for example the event in Hawaii, when an alert of an incoming missile was issued by an employee who accidentally pressed the wrong button that caused panic to spread throughout the island. While the incident was accidental, the consequences for unaccounted human error were devasting.
Take for example the event in Hawaii, when an alert of an incoming missile was issued by an employee who accidentally pressed the wrong button that caused panic to spread throughout the island. While the incident was accidental, the consequences for unaccounted human error were devasting.

 Virtual and Physical Backup Services
Virtual and Physical Backup Services