Top 5 Essentials for Better Cybersecurity
Keep matters simple and make your life easier! Let’s take a look at how we can simplify your online security needs by identifying five essentials you should add to your standard set of cyber security tools.
Basics of Cybersecurity
How does a person distinguish which cyber security programs and installations are necessary? Or which ones require more thought? Simple. We identify the basics of IT security services. Here are the five essential tools that help ensure your online security:
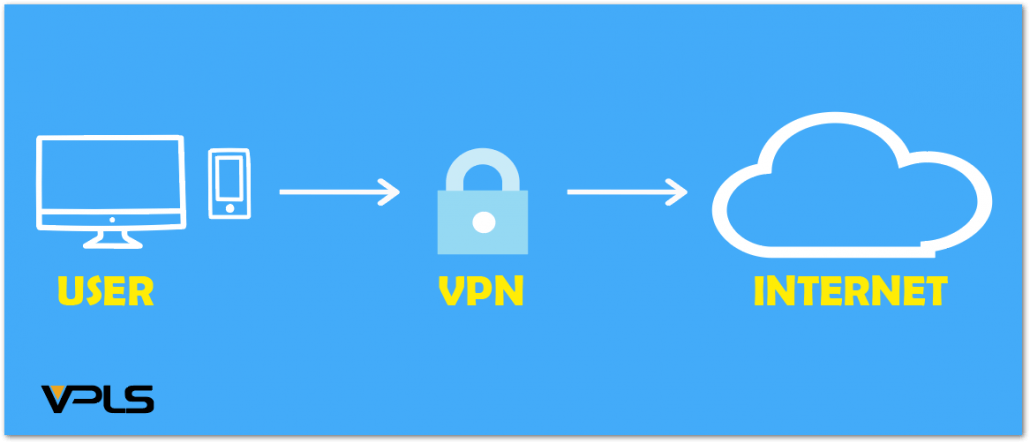
Use a VPN
By using a Virtual Private Network (VPN) you are lowering your risks of attackers preying on your confidential information that you send and receive over the internet. A VPN will secure and anonymize internet traffic by employing encrypted communication and connections. It also creates a virtual point-to-point connection by utilizing virtual tunnelling protocols, traffic encryption and dedicated connections, making it the ideal technology for improved security and privacy protection.
Mediate with a Proxy
The second basic for a secured workstation is to have a proxy. A proxy is a dedicated software or computer that works on computer and is the middleman between your computer and your internet requests. Here is how a proxy works:
- Type in a requested website in your browser.
- The request goes to the proxy, which verifies it via uploaded blacklists of infected websites.
- If the website is safe, the proxy will display it.
- If the website is malicious, the proxy will block it.
- Think of a proxy being a referee; if there is a discrepancy, the proxy will intervene before it can cause any damage.
Fire up your Firewall
Next cyber security essential is installing a firewall. A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on prearranged rules and regulations; they are meant to block your computer from the unannounced or un-requested. Always make sure that you are using a firewall from a reputable source to prevent any unauthorized activity to slip through your computer.
You Can Count on a Reliable Antivirus
Another IT cyber security necessity is a reliable antivirus. Anti-virus software protects your computer by preventing viruses, such as trojans, malware and spyware. The most effective anti-virus products comes with blacklists of infected websites and domains. Equipped with these blacklists, anti-viruses are able to identify and keep harmful malware at bay.
Encrypt Yourself
Finally, you should always try to encrypt your data and information when safeguarding your cyber environment. Encryption is transforming your data or information into a code that cannot be read or understood by the average person. Therefore, when your data is encrypted, cyber criminals would not be able to decode it making their heist completely useless. These five are the key elements to ensuring yourself a safe and hack-proof computer. For those with more advanced and specific needs, these essentials are a good place to start. It’s time that we simplify make our digital lives by protecting ourselves on out there by knowing and understanding the basics of cyber security.
FOLLOW, LIKE & SHARE VPLS!
If you want to keep up with the latest security trends and other IT related products and services, please visit the VPLS blog and stay current with the latest news! Don’t forget! VPLS offers Webroot Managed Malware and Endpoint Protection services that identifies, protects and stops harmful code at the most vulnerable part of the machine.