The Zero Trust Model
Published
Written by
Filed under
 With the ever-increasing number of breaches, it is quite evident that the traditional “trust but verify” model hasn’t been able to withstand today’s cybersecurity threat landscape.
With the ever-increasing number of breaches, it is quite evident that the traditional “trust but verify” model hasn’t been able to withstand today’s cybersecurity threat landscape.
In the “trust but verify” model, the network is divided into either “untrusted” network ( a network connected to the public internet) or “trusted” network (a network connected to the inside of the organization where all the users are trusted and have unrestricted access to anything and everything). As reported by Verizon, 34% of data breaches in 2019 involved internal actors. As a result, trusting anyone, on either side of the perimeter, should not be the de-facto anymore. Thus, it is quite imperative to redesign the network on a Zero Trust Model.
Defining Zero Trust
A Zero Trust Model refers to a threat model where no users, agents, or actors are trusted, irrespective of their location. Instead, all access is based upon a “need-to-know” philosophy and is enforced strictly. This even boils down to cutting off access to any network resource until the user is identified by the network and the need to access the requested resource is proven. Zero Trust Model shifts focus from securing just the network boundaries to securing the network endpoints, which implies a need for redesigning the network from the inside out.
Building a Zero Trust Model
The Zero Trust Model is vendor-agnostic and is built upon the following systems:
Micro-segmentation
Micro-segmentation is a granular approach of segregating the network according to workloads or applications. Virtualization solutions such as VMs and containers, cloud services, and Software Defined Networks (SDNs) are all part of the Micro-segmentation strategy. Being built onto the software, Micro-segmentation comes with an added benefit of reducing the management overhead of the ACLs or the security policies on the firewall.
Identity and Access Management (IAM)
The principle of least privilege should be the modus operandi to implement IAM systems for managing the access to all resources. Technologies such as Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Privileged Access Management (PAM) forms the core of any IAM system.
Log and Analyze Traffic
All traffic traversing through the network should be logged and analyzed. Security information and event management (SIEM) solutions can help easily corelate all the traffic and provide a centralized view to monitor the environment.
In today’s cyber world, it is only logical to assume that there is bound to be a network intrusion. It is not a matter of if; it’s only a matter of when. And when the inevitable occurs, micro-segmentation along with IAM can severely restrict the lateral movement of the intruder, while monitoring all the activities in the network can alert you to any unusual activity. The Zero Trust Model, thus, provides a secure framework to defend against data breaches or any advanced cyber threats.
Interested in learning more about other security tips? Check out this primer on EDR or endpoint detection and response. And learn more about the Managed Security options available from VPLS.
Read More from this Author
If you enjoyed this article, you'll probably like:



 We are excited to announce today that CRN® a brand of The Channel Company, has named VPLS to its 2020 Solution Provider 500 list.
We are excited to announce today that CRN® a brand of The Channel Company, has named VPLS to its 2020 Solution Provider 500 list. 

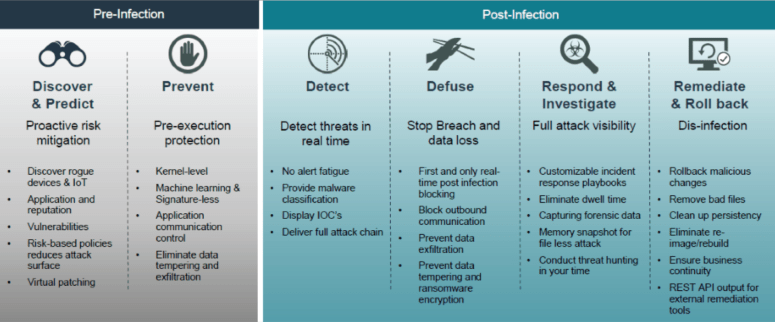
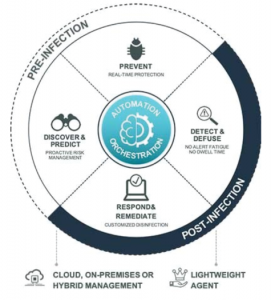 To put it simply, threats will get through your antivirus protection. When they do, EDR will Detect that threat and Respond both quickly and automatically to ensure that the breach is stopped, and that any other relevant actions are taken, such as isolating the endpoint or rolling back malicious changes.
To put it simply, threats will get through your antivirus protection. When they do, EDR will Detect that threat and Respond both quickly and automatically to ensure that the breach is stopped, and that any other relevant actions are taken, such as isolating the endpoint or rolling back malicious changes.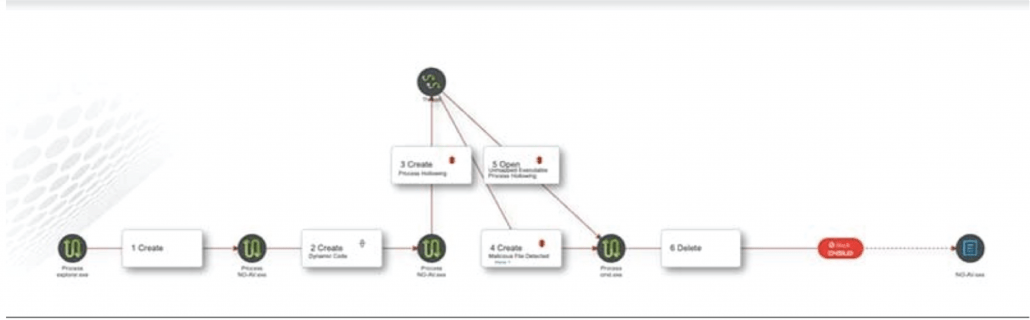








 Schools are implementing more technology into their education programs to keep up with modern technology. Technology makes teaching more efficient since students can learn and do more than they ever could without technology. Even though schools rely on technology, it is not perfect. The advantages that come with technology also comes with some downsides. VPLS talks about the pros and cons of school tech and the policies behind it.
Schools are implementing more technology into their education programs to keep up with modern technology. Technology makes teaching more efficient since students can learn and do more than they ever could without technology. Even though schools rely on technology, it is not perfect. The advantages that come with technology also comes with some downsides. VPLS talks about the pros and cons of school tech and the policies behind it. A student’s phone is their connection to the world, requiring them to carry it around with them to accomplish their everyday tasks. Even if a student’s school phone policy is strict, students will always find a way to use it. However, students don’t always use their phone for unproductive things. Students can use their phones for a variety of academic reasons. Students have apps on their phone, like Quizlet, to help them study.
A student’s phone is their connection to the world, requiring them to carry it around with them to accomplish their everyday tasks. Even if a student’s school phone policy is strict, students will always find a way to use it. However, students don’t always use their phone for unproductive things. Students can use their phones for a variety of academic reasons. Students have apps on their phone, like Quizlet, to help them study.
 Hurricane Florence has tragically hit the East Coast with winds stronger than 80 mph plus tons of rainfall; a recipe for absolute destruction! The fate of homes and businesses alike is uncertain. It is hard to predict when natural disasters like these will strike. The only sure way to protect yourself is to always be prepared for any type of natural disaster at any time.
Hurricane Florence has tragically hit the East Coast with winds stronger than 80 mph plus tons of rainfall; a recipe for absolute destruction! The fate of homes and businesses alike is uncertain. It is hard to predict when natural disasters like these will strike. The only sure way to protect yourself is to always be prepared for any type of natural disaster at any time. In addition to protecting yourself and family, you also have to think about protecting your business. How will your business recover if your office building is destroyed? Storms may do some major damage to your physical workplace and equipment, but your data, on the other hand, can be safe and sound. How? Let’s find out! VPLS offers these solutions to help protect your business’s data from being affected by natural disasters.
In addition to protecting yourself and family, you also have to think about protecting your business. How will your business recover if your office building is destroyed? Storms may do some major damage to your physical workplace and equipment, but your data, on the other hand, can be safe and sound. How? Let’s find out! VPLS offers these solutions to help protect your business’s data from being affected by natural disasters. Utilizing a physical storage place to back up for all your business’s data in your office is not the most secure way to store data. In the event of a break-in or natural disaster at your office, your stored data is at risk of being destroyed. Think of this as putting all of your eggs in one basket. If you leave all your data storage, products, equipment, and other services in your office, everything will be destroyed or lost when disaster strikes. This is all the more reason why you should back up all of your data to the cloud. In the event of a natural disaster, you can rest assured that your data will always be secured in the cloud.
Utilizing a physical storage place to back up for all your business’s data in your office is not the most secure way to store data. In the event of a break-in or natural disaster at your office, your stored data is at risk of being destroyed. Think of this as putting all of your eggs in one basket. If you leave all your data storage, products, equipment, and other services in your office, everything will be destroyed or lost when disaster strikes. This is all the more reason why you should back up all of your data to the cloud. In the event of a natural disaster, you can rest assured that your data will always be secured in the cloud.

 There’s a long list of reasons for why an employer will choose to subscribe to Enterprise Mobility Management services for their big (or small) business needs. Afterall, this cost-effective solution saves businesses money without having to sacrifice any of the essentials.
There’s a long list of reasons for why an employer will choose to subscribe to Enterprise Mobility Management services for their big (or small) business needs. Afterall, this cost-effective solution saves businesses money without having to sacrifice any of the essentials. Today’s EMM technology services come loaded with features. These features vary and are customizable according to your business needs. However, it’s important to understand some features are dependent upon the provider and can vary.
Today’s EMM technology services come loaded with features. These features vary and are customizable according to your business needs. However, it’s important to understand some features are dependent upon the provider and can vary. If you read last week’s VPLS blog,
If you read last week’s VPLS blog, 
 Surveys indicate that businesses offering the flexibility of working from home increases overall productivity in employees and that’s not all! Read the latest VPLS blog for more information.
Surveys indicate that businesses offering the flexibility of working from home increases overall productivity in employees and that’s not all! Read the latest VPLS blog for more information. Vacation days were created to help employees avoid feeling burnt out from work. We all need time to take care of our minds and bodies. Interestingly enough, employees that opt to work from home feel less stressed and are not counting down the days to their next vacation period. Perhaps this is credited to working in an environment that feels familiar and not feeling cooped up in an office all day. Employees are also able to spend more time with their families and recharge their mind and body.
Vacation days were created to help employees avoid feeling burnt out from work. We all need time to take care of our minds and bodies. Interestingly enough, employees that opt to work from home feel less stressed and are not counting down the days to their next vacation period. Perhaps this is credited to working in an environment that feels familiar and not feeling cooped up in an office all day. Employees are also able to spend more time with their families and recharge their mind and body.