Just like everything else in this world, all good matters must come to an end. The once ahead-of-its-time Windows 7 is no exception to the rule. The official end-of-life for Windows 7 is on January 14, 2020. The date is fast approaching, leaving users wondering what action they need to take afterwards. Fortunately, the experts at VPLS can provide the answers to guide you in the right direction to ease your concerns and address all the questions you may have about the aftermath. So without further ado, let’s dive straight into the 5 Things You Need to Know about Windows 7 End-of-Life presented by VPLS:
1. What exactly happens after January 14th, 2020? What does “End-of-Life” even mean?
After January 14th, better known as the official date of “End-of-Life”, Windows 7 users will not receive the automatic updates from Microsoft sites unless they are willing to pay for the extended support. The term “End-of-Life” applies to the idea that there will no longer be any technical support available to assist users with any Windows 7 related matters. A great example of this is Windows XP. You are still able to install it, but the state in which you install it will be the best that it can be; it literally does not get any better–not in a good way.
2. Will Windows 7 still work after End-of-Life?
Users will still be able to install Windows 7, however, they are going to be vulnerable to security threats as there will not be any more updates to upgrade your system against new and advanced cyber threats. It goes without saying that security is the most important aspect of a system!
Fun fact: A couple of years ago, you were able to upgrade Windows 7 to Windows 10 free of charge, but since then, this offer is no longer available. In order to upgrade now, you must purchase it. On the flip side, an offer that is currently ongoing is if you are using Windows 7, Windows 8, or Windows 8.1 Pro and you purchase Office 365 business, Microsoft will provide you with a free license to be upgraded with Windows 10. VPLS offers Office 365 Business and serves as a great way to modernize your system.
3. Should I still use Windows 7?
Just because you can use Windows 7 after expiration, does not mean that you should. It is not advisable to keep on using the software due to the very fact of its vulnerability to cyberattacks, particularly to one called Zero-day, a computer-software vulnerability that is unknown to, or unaddressed by the software maker or antivirus vendors. Although your business might not be aware of the software vulnerability, it might already be known by attackers who are secretly exploiting it.
Pro-tip: It’s good to understand that your defense is in layers – your Operating System (OS) layer is one of your layers of your defensive strategy – it’s just as important as your firewall layer and your network layer. It is unacceptable if your OS layer is not functioning properly.
4. What would be the next steps for anyone to get past their Windows 7?
Go straight to Windows 10. Windows 10 was developed with the consumer’s best interest in mind, being that it is simple to use without needing their technical support. Heed our caution about Windows 8: steer clear from Windows 8! Windows 8 is the antithesis of Windows 10 and was created to be extremely complicated so that users may be super dependent on Microsoft technical support.
5. How does one go about obtaining Windows 10? How can VPLS help?
VPLS provides Windows 10. Additionally, VPLS can help you run a test on your workstation to assess and overcome any incompatibility you may have. A good rule of thumb is that if your workstation is around 7-10 years old, it’s time to replace it. You don’t want to be running computers older than 7 – 10 years old because you are risking them dying on you at any minute, causing data loss.
If you are still on the fence regarding this matter, here are more reasons why you should let go of Windows 7:
Software is going to advance with or without you– people want to use different platforms. Windows 7 would not be able to support the new software because companies will not develop for Windows 7
Hardware will advance without you – you will be left behind – affecting your printers/scanners/cameras/phone.
Ransomware attacks a business every 14 seconds costing companies more than 8 billion dollars yearly!
Vulnerabilities can and will lead you to a plethora of problems that can be costly and long-term.
If you are still planning on keeping and using Windows 7 post “End-of-Life” even after reading these reasons, it’s time to ask yourself these key questions to re-evaluate your thought process: How important is your data? Is your data not important enough where you want to keep it vulnerable?
Finally, if you need one more push to get rid of your Windows 7 after January 2020, consider this: Without defense, criminals can constantly hit your organization with bad emails and phishing links. All it takes is one person in your company on Windows 7 to click on a wrong email or link and it can shut down your entire business…Do yourself a favor; don’t risk it.
To learn more about our Office 365 Services, contact VPLS today!
 It’s never too late to start new cyber security habits so why not start now
It’s never too late to start new cyber security habits so why not start now


 It’s never too late to start new cyber security habits so why not start now!
It’s never too late to start new cyber security habits so why not start now!
 Google Maps displays ransomware attacks against medical, educational and governmental organizations as reported across the US with the Ransomware War Map. This map provides users with the name and industry type of the attacked organization, the location of where the event took place, in addition to the date and time the incident occurred. Also provided with the map is information on whether a ransom was paid to the attacker in the aftermath as well as a link to the full story for those who want to learn more about the attack.
Google Maps displays ransomware attacks against medical, educational and governmental organizations as reported across the US with the Ransomware War Map. This map provides users with the name and industry type of the attacked organization, the location of where the event took place, in addition to the date and time the incident occurred. Also provided with the map is information on whether a ransom was paid to the attacker in the aftermath as well as a link to the full story for those who want to learn more about the attack. 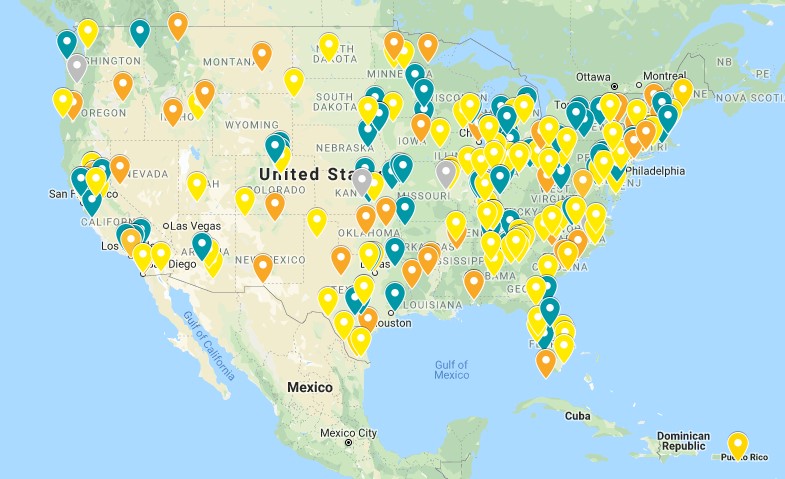

 Backing up your data on a regular basis is one of the most crucial practices for technology users; this ensures that your important data will never be completely gone, hence you have saved it in another form or at another place for safekeeping. On a large scale, enterprises are prime examples of how to properly back up data as they have various sources of backup strategically and conveniently spread out. Their backup sources include an on-premise option, backup stored at a data center, as well as backup stored using cloud services.
Backing up your data on a regular basis is one of the most crucial practices for technology users; this ensures that your important data will never be completely gone, hence you have saved it in another form or at another place for safekeeping. On a large scale, enterprises are prime examples of how to properly back up data as they have various sources of backup strategically and conveniently spread out. Their backup sources include an on-premise option, backup stored at a data center, as well as backup stored using cloud services.


 When it comes to cyber-security, K-12 school districts have more to lose now than before. In addition to new threats and breaches, cyber-security can also prevent schools from achieving and maintaining unique K-12 requirements, such as FERPA and CIP, which can lead to numerous funding and liability issues in the long run. Educational institutions are especially susceptible to a multitude of cyberattacks. Along with unexpected breaches, overlooked access points in data systems can provide cybercriminals an entry to obtain classified and valuable data.
When it comes to cyber-security, K-12 school districts have more to lose now than before. In addition to new threats and breaches, cyber-security can also prevent schools from achieving and maintaining unique K-12 requirements, such as FERPA and CIP, which can lead to numerous funding and liability issues in the long run. Educational institutions are especially susceptible to a multitude of cyberattacks. Along with unexpected breaches, overlooked access points in data systems can provide cybercriminals an entry to obtain classified and valuable data.

 It is a common, but disastrous misconception to think that backup and disaster recovery are the same. This confusion can cause a plethora of data security issues that can potentially hurt the company and damage its brand. Many believe that just a backup alone is enough to prevent data loss in the event of a disaster. However, a backup process is only the beginning stage of a necessary disaster recovery plan. In order to guarantee a business’s data is secured to the fullest, companies need to have a disaster recovery plan in place.
It is a common, but disastrous misconception to think that backup and disaster recovery are the same. This confusion can cause a plethora of data security issues that can potentially hurt the company and damage its brand. Many believe that just a backup alone is enough to prevent data loss in the event of a disaster. However, a backup process is only the beginning stage of a necessary disaster recovery plan. In order to guarantee a business’s data is secured to the fullest, companies need to have a disaster recovery plan in place.