
A new article detailing an SSL VPN certificate vulnerability in FortiGate firewalls is making its rounds in cybersecurity circles. The article details how a FortiGate, if left with its default settings, could allow a man-in-the-middle attack to take place for SSL VPN users.
The article mentions that potentially 200,000 FortiGates are deployed in the wild with the “major security flaw” that this attack exploits.
Fortinet’s response is that they already provide a warning to IT administrators not to use this default configuration, so they will take no action on their part at this time. As of this blog post, no unique CVE number has been assigned to this vulnerability, and the article itself has drawn criticism for reporting as new an already well-known vulnerability that applies to this default configuration.
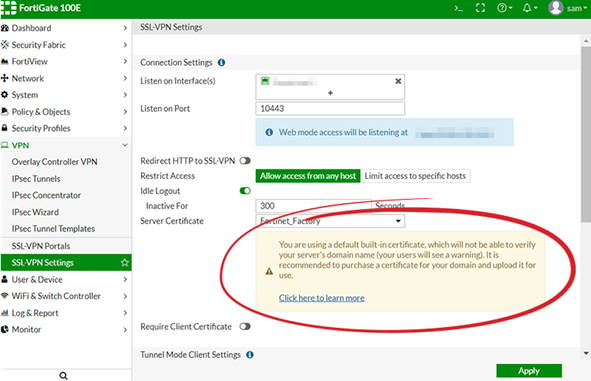
If you are using the default, self-signed certificate for your SSL VPN as shown in the photo above, VPLS recommends purchasing and installing a valid SSL certificate to use for the SSL VPN to mitigate this vulnerability.
Please reach out to us if you would like more information on if this vulnerability applies to your environment and what mitigation steps are required.
Additionally, VPLS would be happy to assist you with the mitigation steps mentioned above, including assistance with purchasing and installing a valid SSL certificate for your VPN, for a $500 flat fee.
Read More from this Author


