VPLS Ranks No. 3918 on the 2020 Inc. 5000 List With Growth of 90.24%
Inc. magazine today revealed that VPLS is No. 3918 on its annual Inc. 5000 list, the most prestigious ranking of the nation’s fastest-growing private companies. The list represents a unique look at the most successful companies within the American economy’s most dynamic segment—its independent small businesses. Intuit, Zappos, Under Armour, Microsoft, Patagonia, and many other well-known names gained their first national exposure as honorees on the Inc. 5000.
"We are proud to be honored on the Inc. 5000 list. In the past year alone, VPLS’s team has nearly doubled and we have significantly expanded our cloud-to-edge service offerings. VPLS is proudly supporting more clients than ever along their IT journeys, and we thank all of our loyal customers, talented employees, and dedicated partners for making this achievement possible.”
said Arman Khalili, CEO of VPLS.
Not only have the companies on the 2020 Inc. 5000 been very competitive within their markets, but the list as a whole shows staggering growth compared with prior lists as well. The 2020 Inc. 5000 achieved an incredible three-year average growth of over 500 percent, and a median rate of 165 percent. The Inc. 5000’s aggregate revenue was $209 billion in 2019, accounting for over 1 million jobs over the past three years.
“The companies on this year’s Inc. 5000 come from nearly every realm of business,” says Inc. editor-in-chief Scott Omelianuk. “From health and software to media and hospitality, the 2020 list proves that no matter the sector, incredible growth is based on the foundations of tenacity and opportunism.”
Read More from this Author









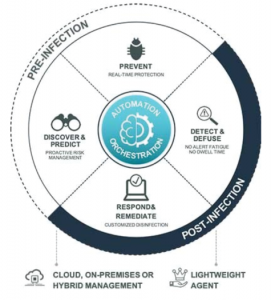 We discuss the what and why of EDR in
We discuss the what and why of EDR in 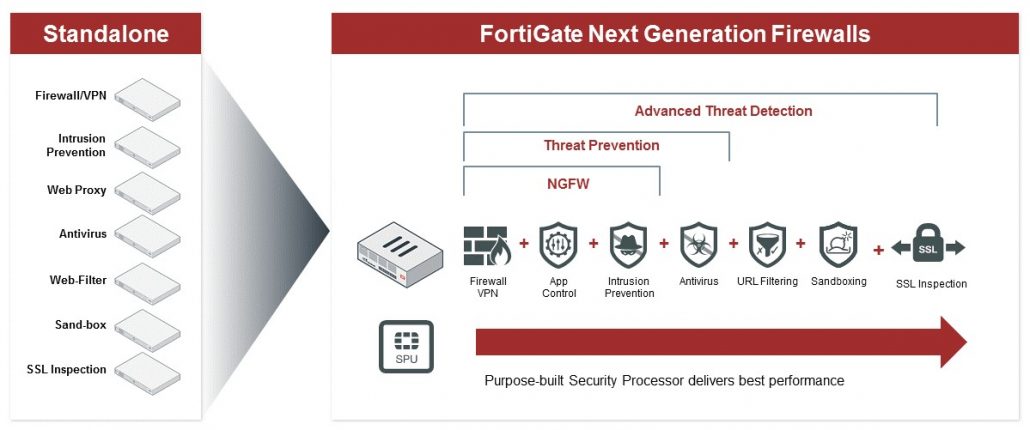
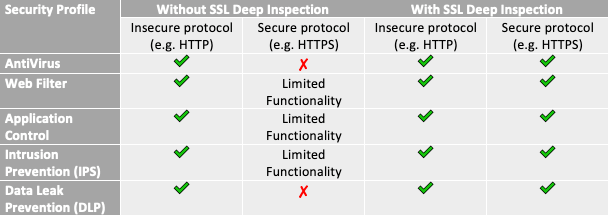
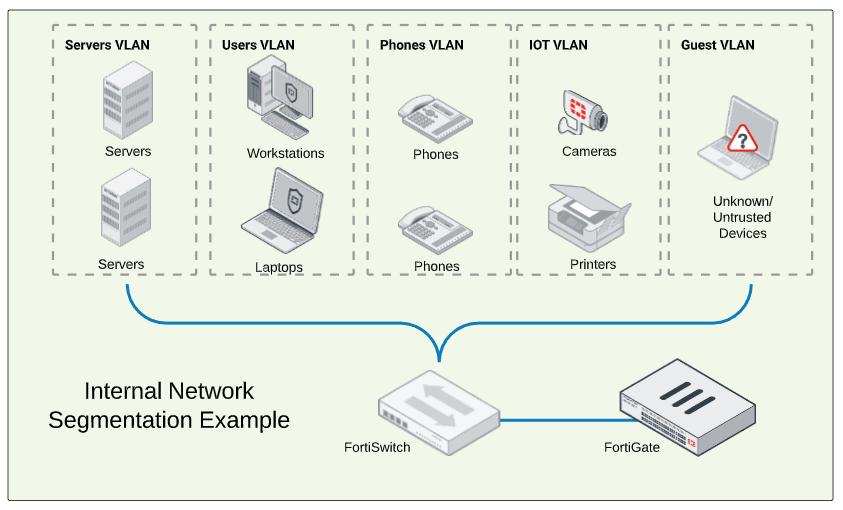
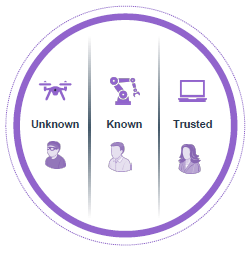 After the NAC solution dynamically allows access based on device trust, endpoint compliance should also be continually evaluated. If the host does not meet compliance requirements, such as if the host becomes infected, does not have antivirus running or it is out of date for too long, or the host does not have the latest OS patches installed, the host should be moved to a restricted quarantine or remediation VLAN until the missing criteria is met.
After the NAC solution dynamically allows access based on device trust, endpoint compliance should also be continually evaluated. If the host does not meet compliance requirements, such as if the host becomes infected, does not have antivirus running or it is out of date for too long, or the host does not have the latest OS patches installed, the host should be moved to a restricted quarantine or remediation VLAN until the missing criteria is met.