
Published
Written by
- John Headley
Filed under

EDR stands for Endpoint Detection & Response. The “endpoint” in this phrase refers to any individual network-connected node belonging to your company, such as an employee’s workstation or a company web server.
EDR emerged because the standard endpoint protection platform (EPP), i.e. traditional antivirus products, were not cutting it in today’s world of ransomware, determined threat actors, and advanced persistent threats (APTs).
“The security mindset has shifted to acknowledge that prevention alone is not enough; security and risk management leaders must be able to more easily harden endpoints and perform more detailed incident response to resolve alerts."
Gartner Research, Magic Quadrant for EPP
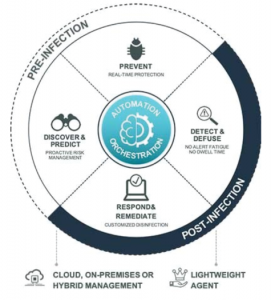 To put it simply, threats will get through your antivirus protection. When they do, EDR will Detect that threat and Respond both quickly and automatically to ensure that the breach is stopped, and that any other relevant actions are taken, such as isolating the endpoint or rolling back malicious changes.
To put it simply, threats will get through your antivirus protection. When they do, EDR will Detect that threat and Respond both quickly and automatically to ensure that the breach is stopped, and that any other relevant actions are taken, such as isolating the endpoint or rolling back malicious changes.
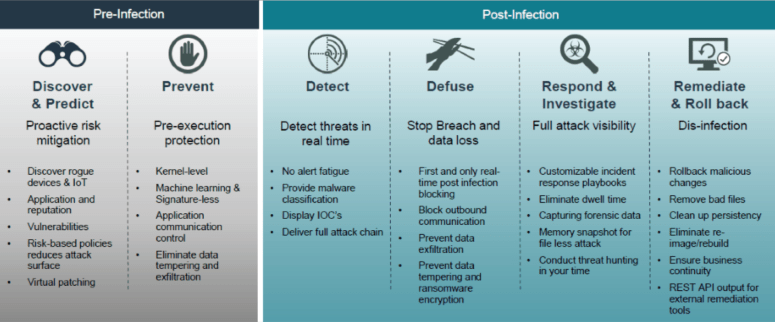
Where EPPs only provide pre-infection protection, EDR completes the circle by providing both pre-infection and post-infection protection.
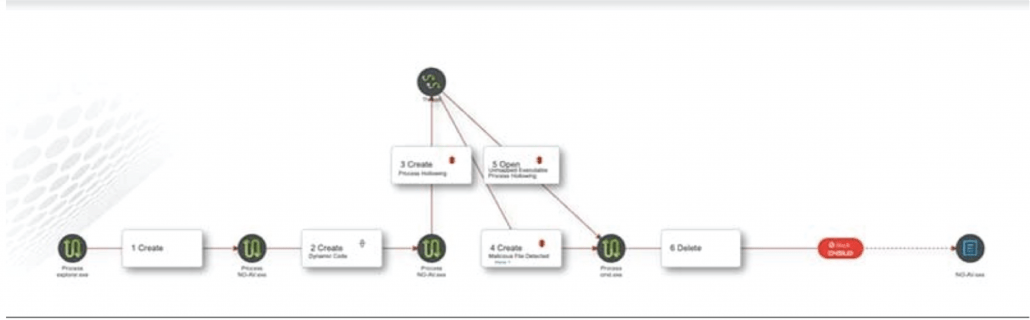
To ensure I am honest on my 5-minute promise, I just wanted to touch on some other capabilities of EDR that set it apart from EPPs. For example, the unprecedented visibility into the endpoint provided by EDR allows your team to investigate the chain of events that led to the attack and understand how the malicious code compromised the system.
Additionally, this visibility allows members of your organization to participate in “threat hunting”, whereby the hunters can look at all of your endpoints for indicators of compromise (IOCs) and proactively investigate the endpoints for threats before a data breach occurs.
There are many more exiting capabilities of EDR, but this primer was meant to introduce those unfamiliar with EDR to the general concepts of the product and how it fits into a company’s security stack. If you are interested in going deeper into how EDR works and how it can fit into your existing environment, please contact us today to learn more.
VPLS recommends and proudly offers FortiEDR as our EDR solution of choice. We are a Fortinet Expert-level partner and MSSP, which means we have highly certified Fortinet engineers (all the way up to NSE8), as well as an in-house SOC, that can deploy and manage FortiEDR for your company with unparalleled expertise.
Read More from this Author


