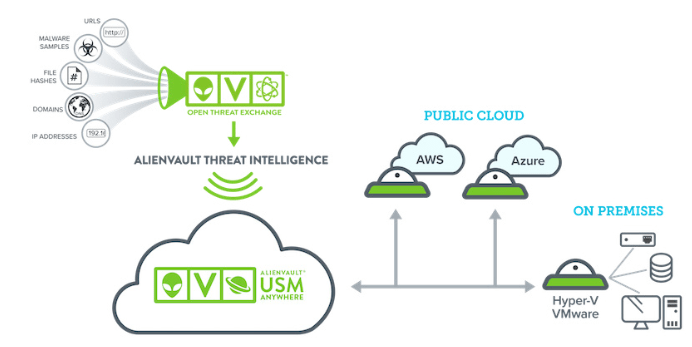
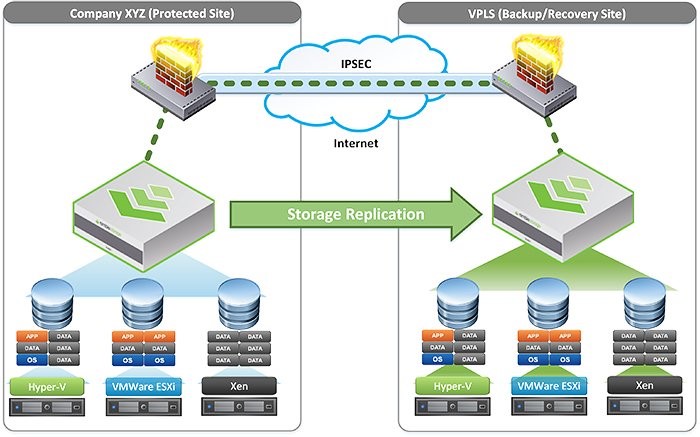
VPLS acquires ZR Systems and expands its managed IT services in Hawaii
Published
Written by
Filed under
We are excited to announce VPLS’s acquisition of ZR Systems, an Aiea-based managed IT services company. The combined company will more effectively serve the growing Hawaiian client base with a range of dedicated onsite support, professional services, and industry-leading software and hardware solutions.
With this acquisition, VPLS expands its data center footprint into Hawaii, bringing its total number of global sites to 19. Additionally, Ricky Zheng, founder of ZR Systems, will join VPLS’s executive management team, bringing more than 20 years of industry experience to his new VP role.
ZR Systems will be known as “ZR Systems, a VPLS company” for a short period following this acquisition. Its expanded service portfolio will now include public and private cloud, bare metal and VPS hosting, colocation, disaster recovery and backup, as well as expanded professional services including managed network and managed SOC services.
Read More from this Author
If you enjoyed this article, you'll probably like:





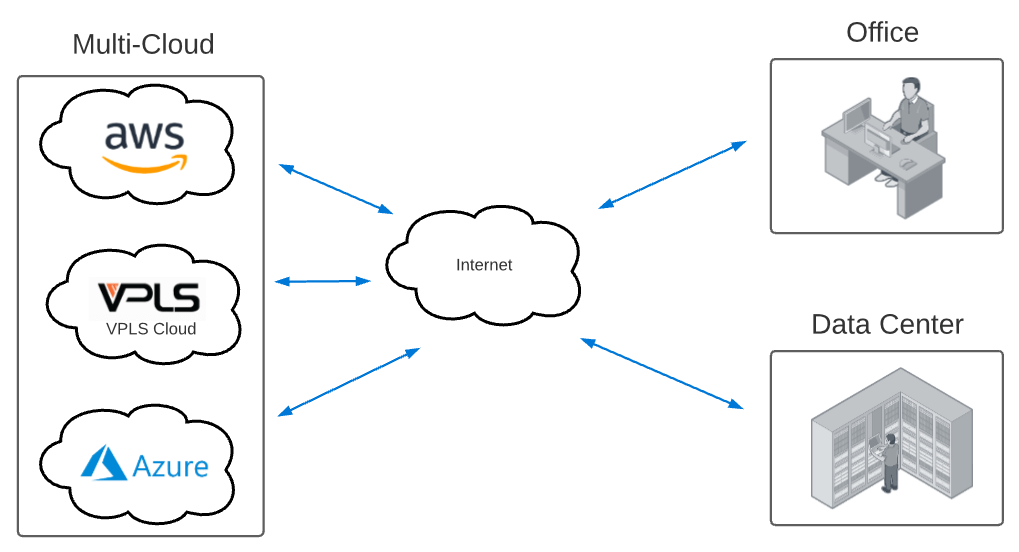 However, while businesses are eager to take advantage of the flexibility a multi-cloud or hybrid cloud environment can offer, providing a consistent user experience to cloud environments over an Internet connection can feel like an uphill battle. Much of the connectivity path will be out of your control, and often riddled with many latency-inducing hops.
However, while businesses are eager to take advantage of the flexibility a multi-cloud or hybrid cloud environment can offer, providing a consistent user experience to cloud environments over an Internet connection can feel like an uphill battle. Much of the connectivity path will be out of your control, and often riddled with many latency-inducing hops.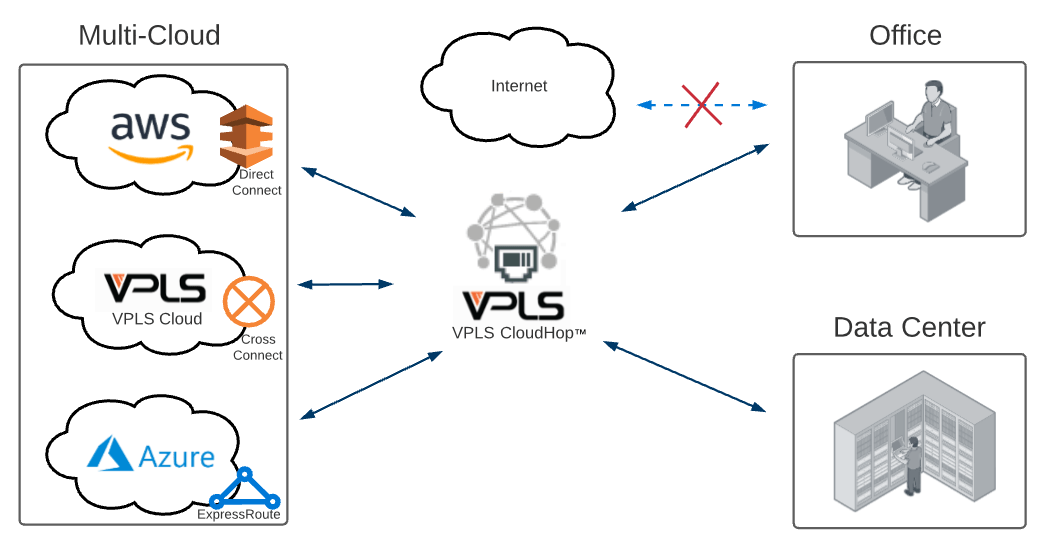 However, with multi-cloud architectures, establishing and managing all of these cloud on-ramps can be an administrative burden. In addition, the more cloud on-ramps you have, the less ROI each of these direct links provide.
However, with multi-cloud architectures, establishing and managing all of these cloud on-ramps can be an administrative burden. In addition, the more cloud on-ramps you have, the less ROI each of these direct links provide. 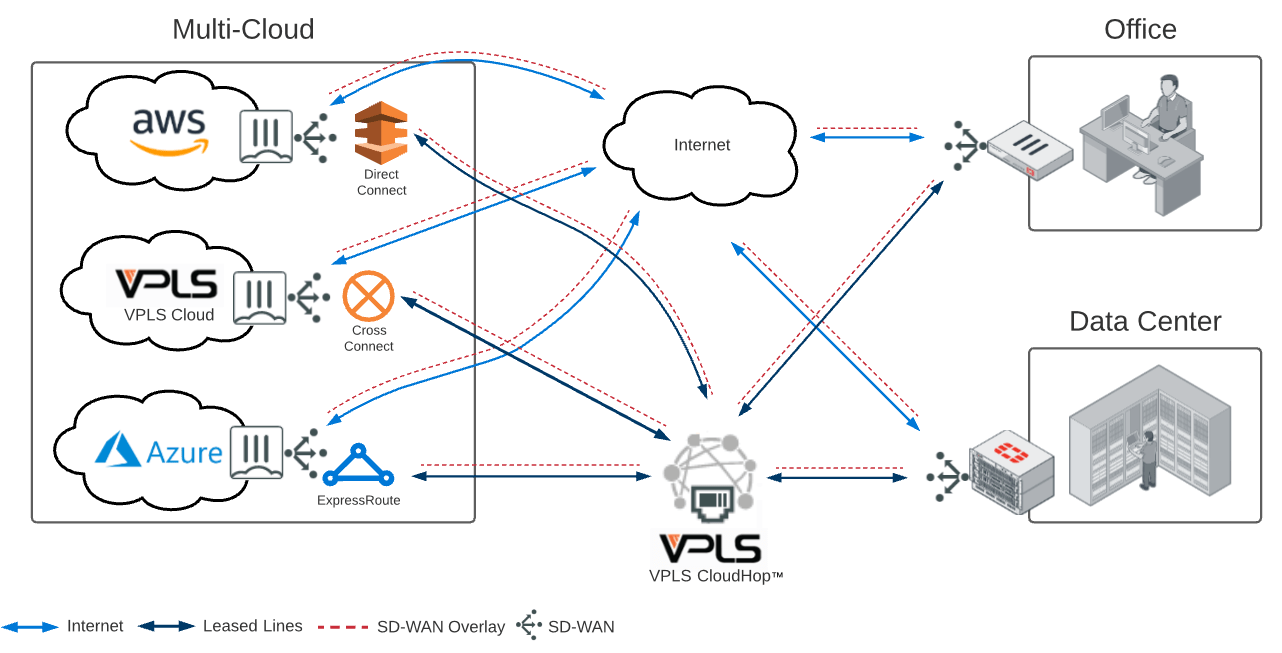


 Many organizations frequently experience challenges with their enterprise wifi that, with the right advice, can be resolved in a few simple steps.
Many organizations frequently experience challenges with their enterprise wifi that, with the right advice, can be resolved in a few simple steps.


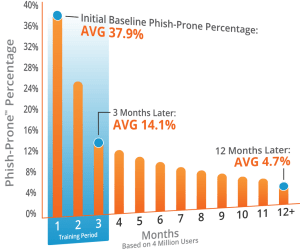
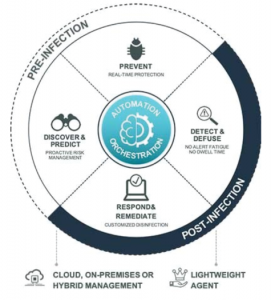 We discuss the what and why of EDR in
We discuss the what and why of EDR in 
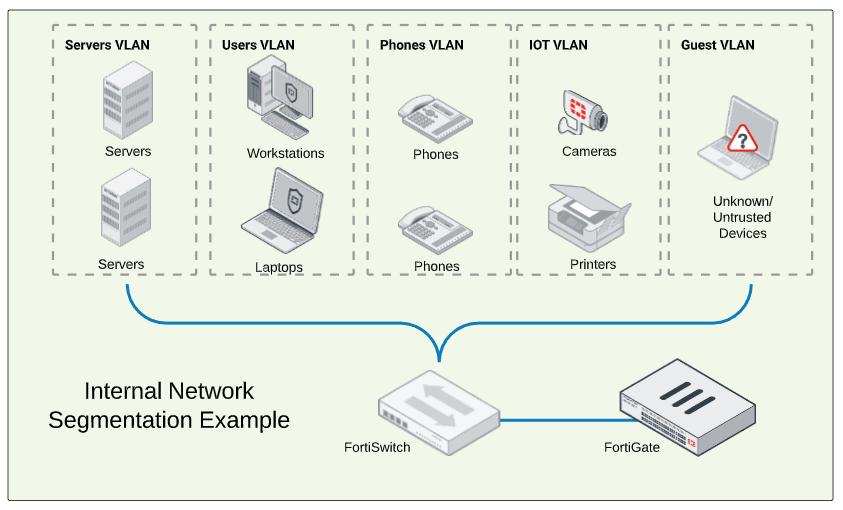
 After the NAC solution dynamically allows access based on device trust, endpoint compliance should also be continually evaluated. If the host does not meet compliance requirements, such as if the host becomes infected, does not have antivirus running or it is out of date for too long, or the host does not have the latest OS patches installed, the host should be moved to a restricted quarantine or remediation VLAN until the missing criteria is met.
After the NAC solution dynamically allows access based on device trust, endpoint compliance should also be continually evaluated. If the host does not meet compliance requirements, such as if the host becomes infected, does not have antivirus running or it is out of date for too long, or the host does not have the latest OS patches installed, the host should be moved to a restricted quarantine or remediation VLAN until the missing criteria is met.