Essential Checklist for Finding the Perfect Cloud Service Provider!
Essential Checklist: Finding the Perfect Cloud Hosting Provider
How can you be certain that your selected cloud hosting vendor is a trusted one who applies the best security practices? Easy! By knowing what questions to ask and recognizing potential red flags.
Without further ado, let’s dive in and go down the checklist of what to look for in a reputable cloud hosting company!
How To Select the Right Cloud Hosting Provider for Your Business
Signing up with a cloud hosting provider can feel overwhelming when you’re not sure what to look for. Additionally, many cloud hosting services tend to splash their site with ridiculous amounts of technical jargon that make it harder for any person to decipher alone.
To better understand what you’re signing up for and what services matter most to your business, let’s go down the list of essential questions and concerns you may want to be answered before proceeding:
Is the provider cloud compliant?
A legitimate cloud vendor may claim that they comply with legalities within the market they sell and service. Sadly, some providers who imply compliance, are really just banking on the compliance of their product and service partners. Be sure to ask details on compliance regulations and where their responsibilities lie when it comes to protecting data privacy.
Will the provider consent to an audit?
An honest cloud vendor will have no problem submitting their services to an audit. This audit should cover both the technology being provided and also the business processes the vendors use to operate those services. Passing an audit regularly is part of a trust-worthy cloud vendor’s normal routine.
Will the provider allow you to define their role and responsibilities?
A transparent cloud vendor will allow you to set clear expectations of what you want the vendor to be responsible for. Ideally, the vendor will meet these customer-defined responsibilities without any problem.
Will the provider deploy and enforce proper data protection standards?
A credible cloud vendor makes sure that their team members are using proper security technology to maintain and manage their services. This includes SSL encrypted connection, a sturdy password policy, and other practices that will guarantee a super secured cloud environment.
Will the provider practice proper cloud security policies?
A reliable cloud vendor knows exactly what security measures to take and when to put them into practice. They are known not only for preventing security breaches but also how to properly handle them should they occur.
Will the provider monitor physical security of the data server?
A responsible cloud vendor’s premises are secured with restricted access to secure equipment as well intricate device logging, to protect movable devices such as laptops and tablets.
Will the provider provide a service level agreement (SLA)?
A professional cloud vendor will continuously comply with all of the Service-Level requirements, inside and out, that were defined in the contract terms without having to be asked to do so.

Searching for the perfect cloud hosting provider doesn’t have to be so scary after all. Just keep this checklist on hand as you navigate towards a safe and reputable cloud hosting environment.
FOLLOW, LIKE & SHARE VPLS!
If you want to keep up with the latest security trends and other IT related products and services, please visit the VPLS blog and stay current with the latest news!
Don’t forget, VPLS offers Hybrid Cloud services that combine the flexibility and agility of putting on or pulling off data from hybrid data centers without compromising compliance and security.



 You may be wondering, “How exactly are these hacks taking place in PUBG and how do they affect me?”
You may be wondering, “How exactly are these hacks taking place in PUBG and how do they affect me?”










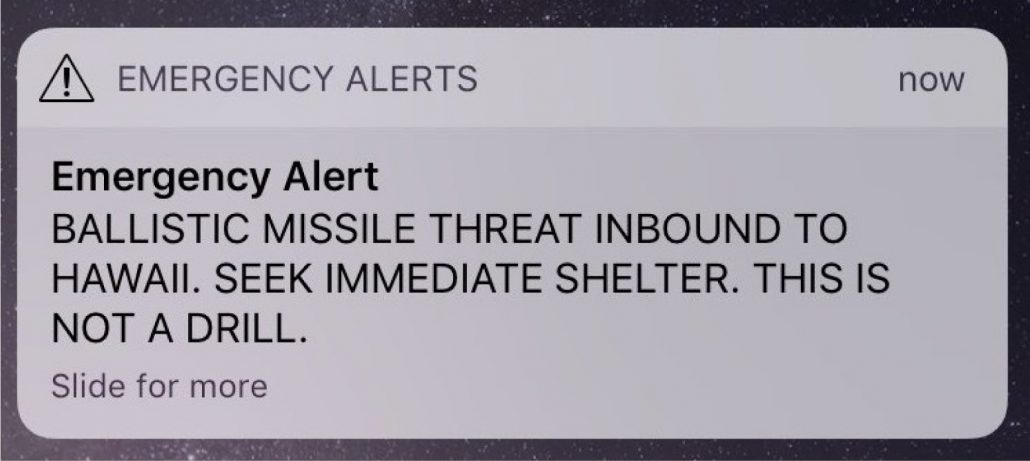 Take for example the event in Hawaii, when an alert of an incoming missile was issued by an employee who accidentally pressed the wrong button that caused panic to spread throughout the island. While the incident was accidental, the consequences for unaccounted human error were devasting.
Take for example the event in Hawaii, when an alert of an incoming missile was issued by an employee who accidentally pressed the wrong button that caused panic to spread throughout the island. While the incident was accidental, the consequences for unaccounted human error were devasting.

 Virtual and Physical Backup Services
Virtual and Physical Backup Services